Subdomain takeovers are now becoming harder and harder to find as people have set up massive automated monitorings to detect subdomain takeovers. It gets a lot harder if you are new to bug bounty as the unique techniques are unknown to you.
So what do you do? Give up? Well since everyone is focusing on enumerating subdomains we can actually look at related domains.
What are related domains?
Related domains are basically registered domains by the companies but they are just not mentioned in the scope. But these are active domains in production that are maybe responsible for running other services so if you take them over you could also takeover active services.
How to takeover related domains?
I have built a platform called SNIFFCON which has a subdomain scanner that actually looks for such related domains and gives output like this:
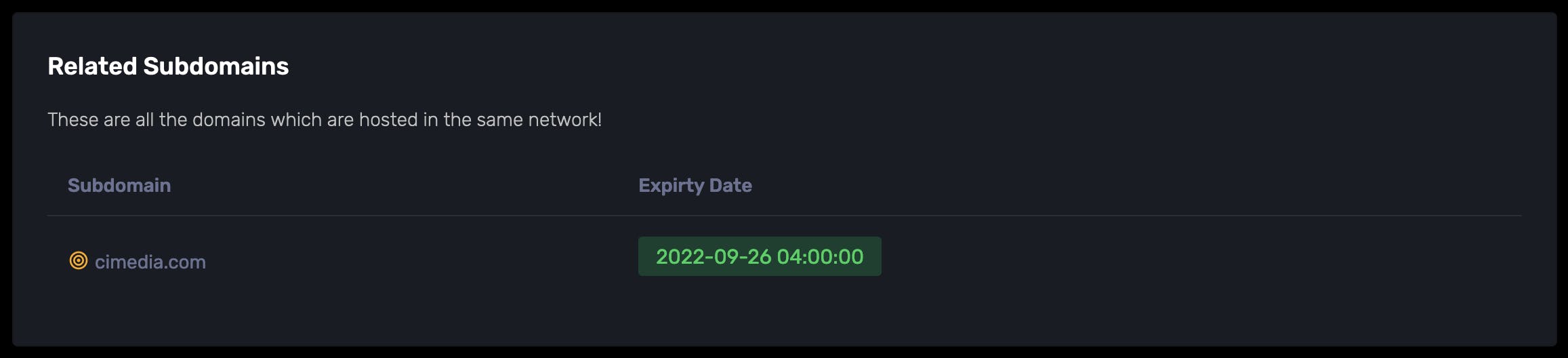
But you can also find related domains here: https://otx.alienvault.com/indicator/domain/media.net
As you can see OTX provides a lot of false-positive results for related domains but SNIFFCON managed to find the actual domain that belongs to that company.
After identifying the related domains you need to find the domain expiry date because usually, companies forget to renew these low priority domains and expose themselves to critical vulnerabilities because some of the servers might try to communicate with that expired domain. Attackers can implement a TCP dumper in the website to start capturing sensitive data.
SNIFFCON has a whois monitoring tool that allows you to monitor these domains and alerts you when they are expired so you will need something like that to start taking over these related domains as soon as they get dropped.


