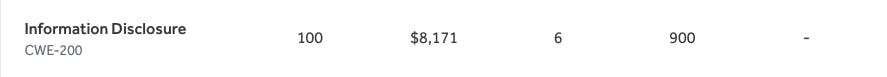Photo by Daan Mooij on Unsplash
The "Unsubscribe Tragedy" That Exposed 200000+ User Data On Search Engines
How my "Unsubscribe Tragedy" could have been another security nightmare? 🤔
This happened in 2018 when I was a regular bug bounty hunter, At that time CloudBleed was still trending. So as a young hacker full of enthusiasm I tried to find something similar and then I ended up finding the "Unsubscribe tragedy"!
So why am I sharing it now? I didn't get permission to disclose it at that time but I think since the issue still exists in the wild, we should talk about it.
This happened when I was receiving too many emails from a particular company and I wanted to unsubscribe from their newsletter, So I noticed the "Unsubscribe Button" and basically unsubscribed from the newsletter. But few things were stuck in my mind when I visited the unsubscribe page, they are:
- It had information such as my email, address, and phone number
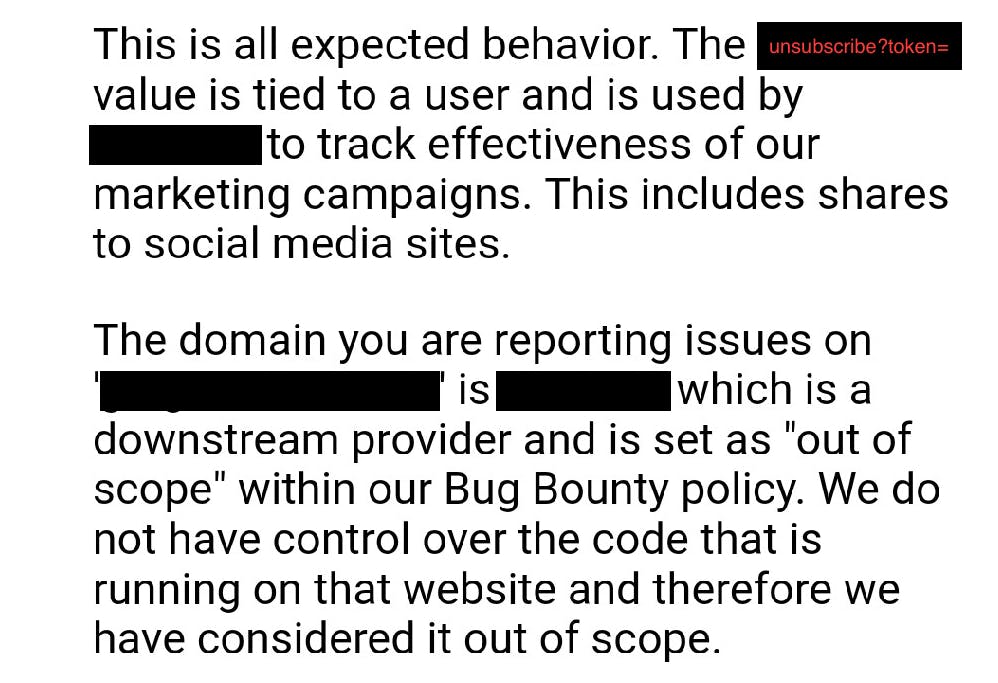
- And the unsubscribe token was more like a tracking token also which was getting used throughout the website. (How did I know? Because the moment I went to their homepage from the unsubscribe page the token also followed along)
After a few days, I was trying to understand and study the cloudbleed issue and then it came to my head that I can try my luck there on that unsubscribe page since it was also throwing the token everywhere then technically it should also be leaking somewhere.
My first plan was to find the company behind that marketing software because I knew companies wouldn't allow third-party branding for their own usage. Luckily that company using the marketing software was in hackerone so by risking my reputation knowing it's an out-of-scope vulnerability I still reported it to know what software they used. Because my strategy of going through HTML source codes to find any traces of the software didn't help much so this was the only option.
So basically I reported an issue to the company based on my 2nd observation, saying that it was leaking the token to social media sites because that page also had links to their twitter/facebook pages so when I clicked on it the token was also getting captured there by those social media sites.
And the unsubscribe token was more like a tracking token also which was getting used throughout the website. (How did I know? Because the moment I went to their homepage from the unsubscribe page the token also followed along)
And it worked! We got the company!
After knowing the company name I was quite shocked to find out that it was one of the leading marketing software at that time and even they were getting ready to be acquired by Adobe. So after this, I instantly knew if I find any issue regarding this it will affect a massive userbase. That just motivated me even more to find something in it, I was working for days to find out how I can leak the token at a mass level, and then it hit me, Why am I trying to leak it? Since the token gets tied to any URL user visits, it should get archived or cached by something somewhere.
First guess? Obviously! Google!
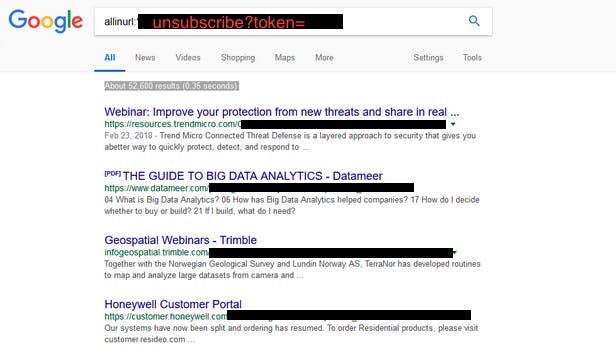
So google was giving us 50k+ results for the tokens but it got interesting when I searched it on bing.
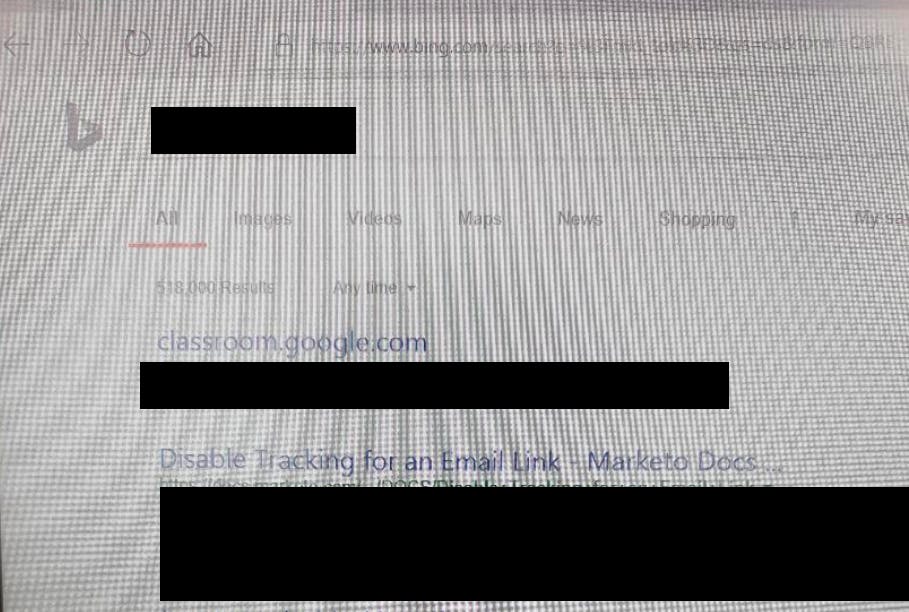
(Sorry for the blurry screenshot, this is the only photo I had to proof the bing results)
I was getting 500k+ results on bing, I think google was restricting a lot of results due to region and other settings but seeing the results on bing convinced me that yes this is something that needs to be reported.
I directly reached out to the CISO of the company on linkedin and he was a nice guy who instantly connected back to me and we had few meetings and then they decided to fix the issue. Even though they didn't have any bug bounty program they decided to reward me still.

By the way, I never managed to use the money on that card because it would only work in the US but did I make any money out of it?
Well, yes I did. Because the CISO told me they implemented a new configuration where users can choose to not leak that token and I knew what to do then, Just find the vulnerable ones which are misconfigured and report them.
Voila...
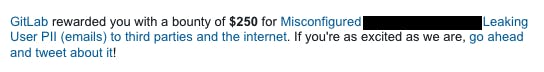
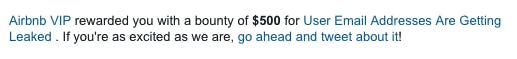
And Many more...
Let's say most of my earnings for "Information Disclosure" came from this one "Unsubscribe Tragedy" because it only takes 2-3 minutes to find and report.